Microsoft Dynamics GP network data encryption
If your organization happens to be PCI-compliant you are already too familiar with the data encryption requirements imposed by the financial institutions you currently deal with.
As part of your certification and compliance process, you probably had to find a way to encrypt customer and credit card data traveling between your organization and the credit card processor. This means you had to enable SSL encryption on your servers all the while obtaining a certificate issued by a certificate authority.
But what about your customer data traveling between your SQL Server and your Microsoft Dynamics GP client, and viceversa.
Here are three methods to encrypt Dynamics GP data traveling over the network:
1) You can enable strong data encryption at the DSN level if using a Microsoft SQL Server Native Client DSN to connect to your Dynamics GP databases on a Microsoft SQL Server 2005 or Microsoft SQL Server 2008 database server. To enable encryption, check the Use Strong Data Encryption option on the 4th dialog page, as shown below.
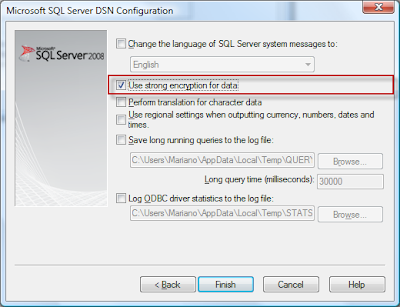
If using this option, you will want to make sure it's enabled on all workstations, and provide a centralize way to administrate it, for example, via the Group Policy Data Sources preferences extension.
2) To encrypt data traveling from clients to server, you can use Microsoft SQL Server Configuration Manager to configure the SQL Server Native Client protocols used to communicate to the SQL Server Database Engine.
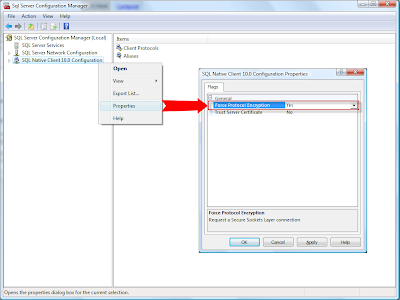
The Force protocol encryption option will request a connection using SSL.
When Trust Server Certificate is set to No, the client process attempts to validate the server certificate. The client and server must have each have a certificate issues from a public certification authority. If the certificate is not present on the client computer, or if the validation of the certificate fails, the connection is terminated.
When set to Yes, the client does not validate the server certificate, thereby enabling the use of a self-signed certificate.
Trust Server Certificate is only available if Force protocol encryption is set to Yes (See method 3).
3) You can use Microsoft SQL Server Configuration Manager to setup a server side certificate, preferrably issued by a certificate authority. To encrypt connections, you should provision the SQL Server Database Engine with a certificate. If a certificate is not installed, SQL Server will generate a self-signed certificate when the instance is started. This self-signed certificate can be used instead of a certificate from a trusted certificate authority, but it does not provide authentication or non-repudiation.
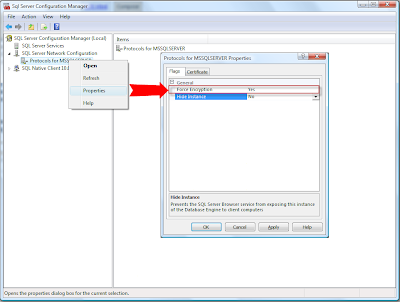
NOTE: Secure Sockets Layer (SSL) connections encrypted using a self-signed certificate do not provide strong security. They are susceptible to man-in-the-middle attacks. You should not rely on SSL using self-signed certificates in a production environment or on servers that are connected to the Internet.
The login process is always encrypted. When Force Encryption is set to Yes, all client/server communication is encrypted, and clients connecting to the Database Engine must be configured to trust the root authority of the server certificate.
While your organization may not necessarily be seeking PCI-compliance, having strong data encryption for your accounting data is just another way to position your company with customers and vendors.
Related Articles
Encryption Connections to SQL Server - Microsoft SQL Server Books Online.
How to: Enable Encrypted Connections to the Database Engine (SQL Server Configuration Manager) - Microsoft SQL Server Books Online.
Until next post!
MG.-
Mariano Gomez, MVP
Maximum Global Business, LLC
http://www.maximumglobalbusiness.com
As part of your certification and compliance process, you probably had to find a way to encrypt customer and credit card data traveling between your organization and the credit card processor. This means you had to enable SSL encryption on your servers all the while obtaining a certificate issued by a certificate authority.
But what about your customer data traveling between your SQL Server and your Microsoft Dynamics GP client, and viceversa.
Here are three methods to encrypt Dynamics GP data traveling over the network:
1) You can enable strong data encryption at the DSN level if using a Microsoft SQL Server Native Client DSN to connect to your Dynamics GP databases on a Microsoft SQL Server 2005 or Microsoft SQL Server 2008 database server. To enable encryption, check the Use Strong Data Encryption option on the 4th dialog page, as shown below.

If using this option, you will want to make sure it's enabled on all workstations, and provide a centralize way to administrate it, for example, via the Group Policy Data Sources preferences extension.
2) To encrypt data traveling from clients to server, you can use Microsoft SQL Server Configuration Manager to configure the SQL Server Native Client protocols used to communicate to the SQL Server Database Engine.

The Force protocol encryption option will request a connection using SSL.
When Trust Server Certificate is set to No, the client process attempts to validate the server certificate. The client and server must have each have a certificate issues from a public certification authority. If the certificate is not present on the client computer, or if the validation of the certificate fails, the connection is terminated.
When set to Yes, the client does not validate the server certificate, thereby enabling the use of a self-signed certificate.
Trust Server Certificate is only available if Force protocol encryption is set to Yes (See method 3).
3) You can use Microsoft SQL Server Configuration Manager to setup a server side certificate, preferrably issued by a certificate authority. To encrypt connections, you should provision the SQL Server Database Engine with a certificate. If a certificate is not installed, SQL Server will generate a self-signed certificate when the instance is started. This self-signed certificate can be used instead of a certificate from a trusted certificate authority, but it does not provide authentication or non-repudiation.

NOTE: Secure Sockets Layer (SSL) connections encrypted using a self-signed certificate do not provide strong security. They are susceptible to man-in-the-middle attacks. You should not rely on SSL using self-signed certificates in a production environment or on servers that are connected to the Internet.
The login process is always encrypted. When Force Encryption is set to Yes, all client/server communication is encrypted, and clients connecting to the Database Engine must be configured to trust the root authority of the server certificate.
While your organization may not necessarily be seeking PCI-compliance, having strong data encryption for your accounting data is just another way to position your company with customers and vendors.
Related Articles
Encryption Connections to SQL Server - Microsoft SQL Server Books Online.
How to: Enable Encrypted Connections to the Database Engine (SQL Server Configuration Manager) - Microsoft SQL Server Books Online.
Until next post!
MG.-
Mariano Gomez, MVP
Maximum Global Business, LLC
http://www.maximumglobalbusiness.com
Comments